Passwords act as a universal security solution that protects online accounts from cybercriminals by preventing unauthorized access. But as cyberattacks become more prevalent and sophisticated, especially in the time of the COVID-19 pandemic, passwords are no longer enough to mitigate the risk of attacks.
Customer Portal | Washington: 206-725-7728 |
Oregon: 503-208-7777
Blog
Blog
Don’t be a victim of juice jacking

Smartphones have become an indispensable tool for most of us. We use them for a wide range of activities, from gaming to checking social media to accessing work apps. Because of heavy use, our smartphones may sometimes run out of battery. When that happens and you’re out in public with no access to your charger, using public charging kiosks to bring your phone back to life can seem like a good idea — but it’s not.
What you need to know about Mac ransomware
Data storage: HDD and SSD defined
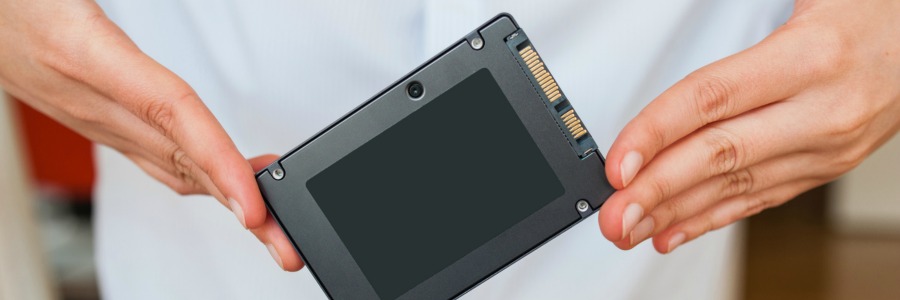
When purchasing new computers, buyers used to have limited choices when it came to what kind of storage they got with their laptop or desktop PCs. But nowadays you can configure your system with either traditional hard disk drives (HDDs), increasingly common solid state drives (SSDs), or in some cases both.
VoIP’s hold message options are easy

Being put on hold can be a bothersome experience for customers. Unless they have absolutely nothing else to do, people dislike waiting for an indefinite amount of time and achieving nothing. But did you know that when you make customers wait on the other end of the line, you actually have the opportunity to provide them with informative messages? With Voice over Internet Protocol (VoIP), this is very easy to do.
Is your web browser safe enough?
What are Microsoft 365 Groups connectors?

Microsoft 365 Groups is a cross-application service that lets users choose the people with whom they want to collaborate and share resources, such as a document library or a Microsoft Outlook inbox. And with its connectors feature, anyone can send information — even those from third-party apps — to the rest of the group right in their shared inbox.
How business intelligence can help small busine
What’s in store for Windows users in 2021?
Two excellent ways to verify user identity

A secure login process is an excellent way to protect your business from cybercriminals.
When it comes to verifying user identity, you can choose between two-step authentication and two-factor authentication. Learn the difference between the two so you can have a better appreciation of your cybersecurity options.





