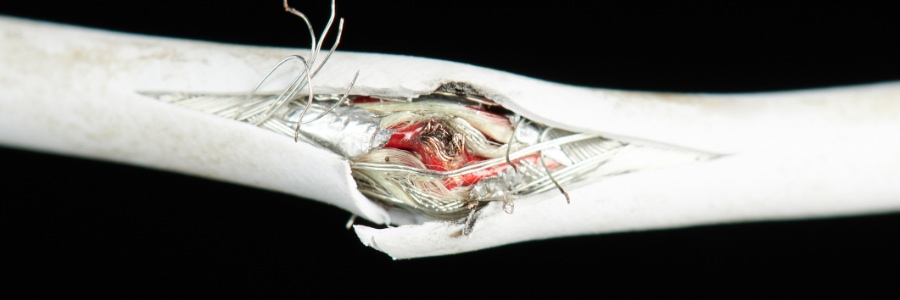
Copper Clad Aluminum
Recently we have seen a re-emergence of “less than” quality of copper cabling for structured cabling solutions. When following up to see how my quotes were progressing, we were being told that we were considerably higher than our competition.